More information security or a better user experience?
In corporate IT solutions, more information security normally results in lower user experience, and vice versa. Low security level threatens our operations, but poor user experience increases the risk that employees will simply refuse to use the new solution.
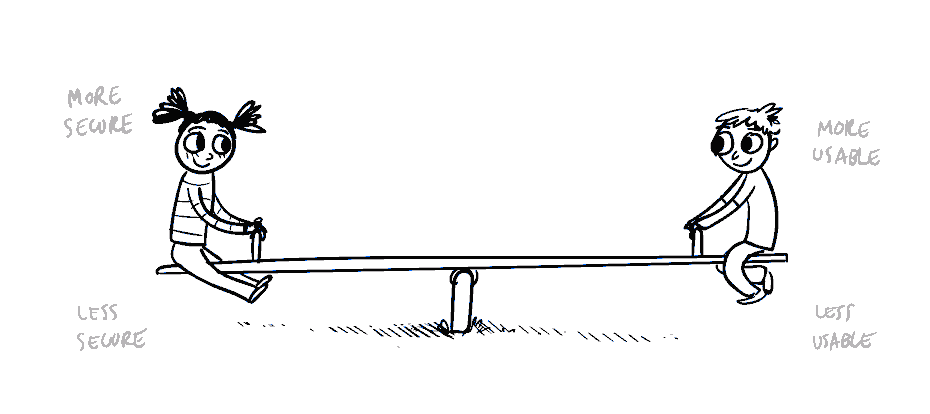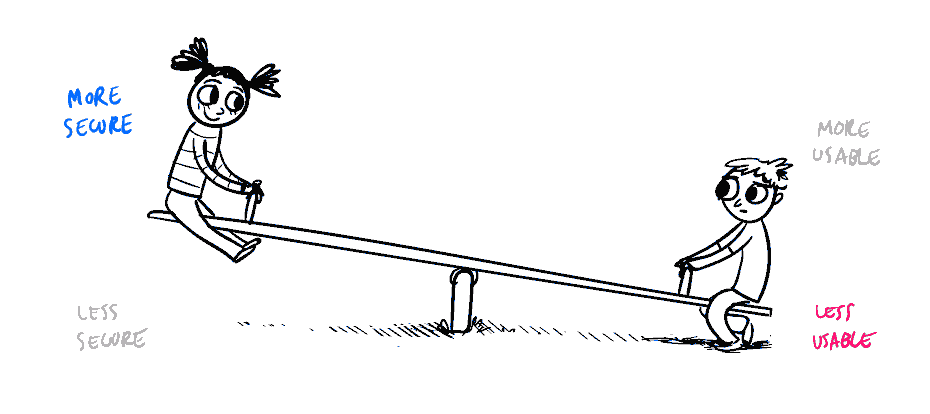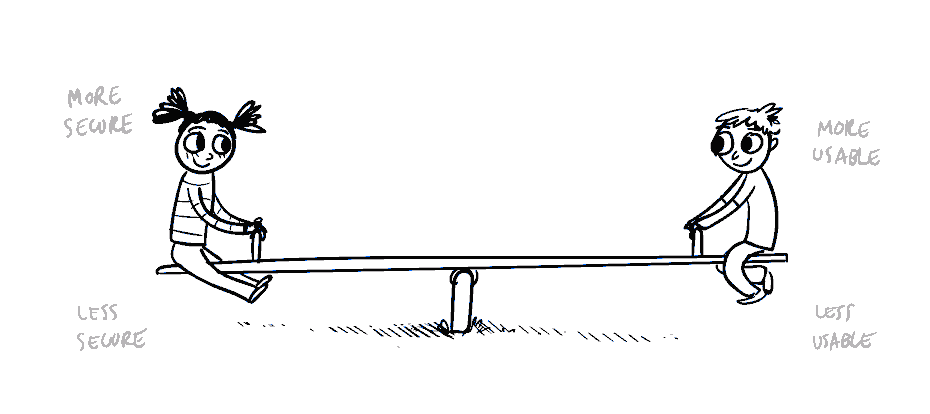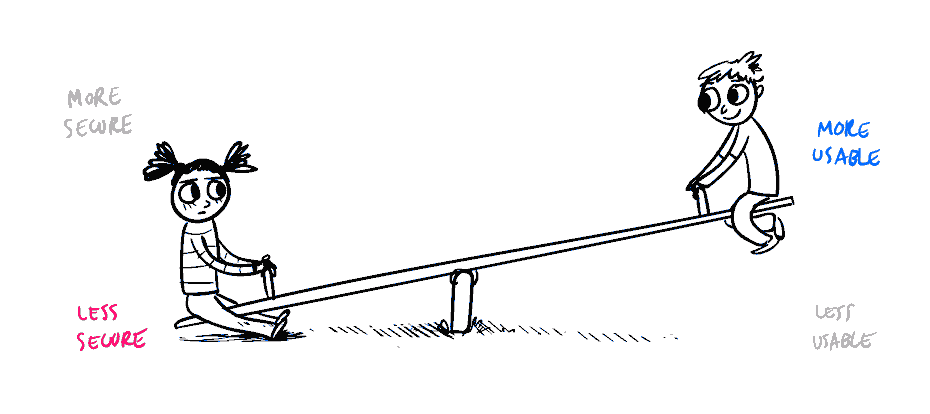
© Medium, 2018
However, document management and storage do not allow for such compromises and require both. Therefore, we have already considered both aspects when planning the capacity of the InDoc EDGE information management platform. Let's see how.
Zajem ali uvoz dokumentov
Capturing documents in a document management system is one the first steps of digitalization. Paper documents are scanned, and documents in electronic format are captured at source or imported at a later date.
This raises a very important question: how to simplify capture and make it easier for users to start working? To deliver on that promise, InDoc EDGE solutions are connected with source information systems (e.g. ERP or CRM) without any risky intermediary repositories. For each document received, InDoc EDGE will return the SHA value for received content.
- In order to be able to retrieve documents easily and correctly at a later date, they must be classified, labelled and indexed properly upon capture.
Access do documents
When the document is placed in the document management system, accessing it is a simple task (if the document is properly indexed and searchable, of course). Potential problems are linked to huge quantities of different types of documents, e.g. contracts, invoices, and order forms. Quality assistance in the phase of setting up management for large volumes of different types of documents and InDoc EDGE’s advanced search options will reduce the time spent on searching for the information.
On the other hand, all users may not be granted access to all documents. Documents containing personal data are particularly sensitive. InDoc EDGE provides various levels of access to documents and recording activities in the audit trail. It also supports the option of requesting the user to state the reason for viewing the content of documents that contain personal data.
- The decision of user roles and rights is one of the most complex tasks and a precondition for an efficient implementation of solutions for managing documents and operational processes.
Sharing documents
Sometimes we need to share confidential documents with third parties outside the company. In terms of information security, sharing documents poses a considerable risk, since documents may be intercepted and misused by an unauthorized person. Electronic mail is a common channel of document exchange, but its file size restrictions create another problem for sharing large files.
To avoid the above issues, we have enabled supervised sharing of documents directly from InDoc EDGE. You can simply select the document you wish to share, enter the recipient’s e-mail address, the purpose of sharing, password and viewing expiry date. The recipient will receive a custom link to the document and password via two separate channels, and the document will only be available within the specified time period. Recipient access is controlled and captured in the audit trail along with the purpose of viewing.
- Sharing files that contain personal data by electronic mail or exchanging them through cloud storage is a priority concern in guaranteeing compliance with the GDPR.
Long-term electronic document storage
When we no longer need to use a document every day, it is transferred to an electronic archive. Long-term preservation creates new challenges in terms of usability and security. Documents will be kept for 10, 30 or even 50 years, and during this time we have to ensure their availability, usability, integrity, authenticity and permanence.
For that reason all documents entering InDoc EDGE are first converted into a file format suitable for long-term preservation, and automatically digitally signed and time stamped. InDoc EDGE regularly renews its time stamps, thereby ensuring the validity of the digital certificate at the time of signing. On the other hand, the risk of repeated digital signing of documents using new and improved cryptographic algorithms is being reduced due to rapid development of encryption methods and capabilities.
- We know that in time file formats, standards and access to documents will change, and the validity of digital certificates used to sign the document will eventually expire.
All documents in the document management system and the certified e-storage system are further encrypted. InDoc EDGE users do not notice strong encryption since the system automatically performs decryption to plain text. Thanks to enhanced encryption, unauthorized direct access to content in the database or file system is effectively prevented in case of a hacking attempt or data theft.
© Medium, 2018
So when is there too much information security? We believe that digital business does not tolerate any such compromises and simply requires both. Is that simple to achieve? No, definitely not, especially in this time of rapid change when agility and continuous development are key.
Want to know more? Contact us!


